Cypherock is BIP39 compliant
To make key management compatible, most of the wallets implement hierarchical key derivation. A hierarchically derived wallet generates keys using BIP39 and BIP32 proposals in the following
fashion:
ENT--> Mnemonics--> BIP39 Seed--> Master Node--> Purpose Node--> Coin Node-> Account Node--> Change Node--> Address Index Node.
ENT stands for entropy bits and is generated using XOR of hardware-based TRNG from STM32L4 which has a NIST-compliant Deterministic Random Bit Generator (DRBG) & random nonce generated from Atecc608a secure element(FIPS 800-90 A/B/C RNG) in the X1 Vault. Its length may be chosen anywhere between 128 to 256 bits with increments of 32 bits.
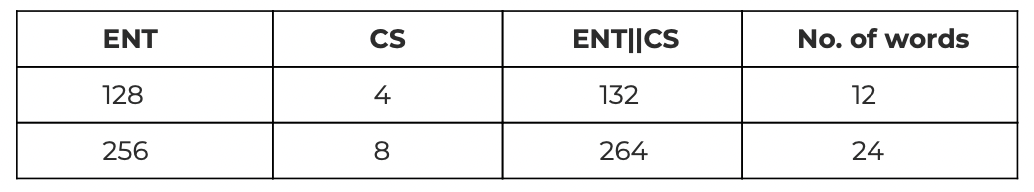
CS stands for checksum and represents the first ENT/32 bits of sha256(ENT). The CS bits are appended after ENT which is represented as ENT||CS. In ENT||CS each group of 11 bits represents a number between 0 to 2048 which represents a unique word in the BIP39 wordlist. The group of words represents mnemonics, also called seed phrases, which are used to recover a wallet in case a user wants to regenerate keys on a different machine.
From the above table, it could be noticed that Mnemonics and ENT are interconvertible. In Cypherock’s implementation, we apply Shamir’s secret sharing algorithm on ENT. In a standard HD wallet, different key pairs are used for every transaction, and the derivation of private keys from mnemonics is a one-way operation. Hence to make backup simple and easy we apply SSS on ENT instead of any private key. Applying SSS on ENT also enables us to derive mnemonics on reconstruction.
Shamir's Secret Sharing scheme is applied separately to each byte of the ENT and GF(256) is used as the underlying finite field. Bytes are interpreted as elements of GF(256) using polynomial representation with operations modulo the Rijndael irreducible polynomial x8 + x4 + x3 + x + 1. We apply 2 of 5 Shamir’s secret sharing algorithm where the secret byte is considered at index x= 0 and the subsequent shards are considered at indices x=1, x=2, x=3, x=4 and x=5 of the finite plane. The coefficients of polynomials are generated using the hardware-based random number generator. A user-defined password is used to symmetrically encrypt the secret byte array before transferring them to the X1 Cards. The data stored inside each X1 Card is as follows:
Wallet Name
The double hash of the password
Password encrypted shard
MAC of the encrypted shard
Nonce
Shard Index
SizeofENT
Scheme
Checksum of the data
We use chacha20 for encrypting the shard with the hash of the user-defined password. MAC is used to authenticate the decrypted shard. Double hash is used for password verification inside the X1 Cards. Although the X1 Card uses EAL6+ secure element, using a double hash of password for authentication and hash of the password for symmetric encryption ensures that even if the data inside the X1 Cards gets breached, getting original shard remains tremendously difficult.
Last updated